PodChats for FutureIoT: Securing IoT beyond 2022 – Technologist
According to IoT analytics, the current business sentiment for companies in digital and IoT remains predominantly positive. There is widespread acknowledgement that Covid-19 had an overall positive effect on the accelerated adoption of IoT technologies.
IoT Analytics also reports record levels of VC investments for IoT firms, including acquisitions in the areas of AI and analytics. It is anticipated that despite headwinds like rising inflation and prolonged supply chain disruptions, overall sentiment will continue to be positive as the number of connected IoT devices reach 14.4 billion by the end of 2022.
With this growth, we can expect more targeted and perhaps creative ways of attacking both producers and enterprise consumers of IoT devices in the years ahead.
According to Satyajit Sinha, principal analyst for IoT Analytics, organisations tend to focus on security from a softer aspect or had network security at best.
“We have never seen security from the device aspect, and IoT demands different requirements of security such as authentication, authorisation, and identification. Most devices are secured through software security which is not adequate as they are vulnerable to attacks.”
Satyajit Sinha
“The more we create awareness about IoT devices security, the more people will implement security in their devices,” he added.
How adequately do you think current IoT ecosystems are secured, especially for unmanaged IoT devices?
Satyajit Sinha: The IoT devices do not have the capability to hold a higher level of security because of the power constraint thus security will always be a challenge. However, if these devices are connected to a gateway or a router, they can secure the touchpoint of the network and IoT ecosystems. It is not the case for small devices or unmanned devices.
Are concerns around IoT security justified? Or why does the IoT ecosystem require security?
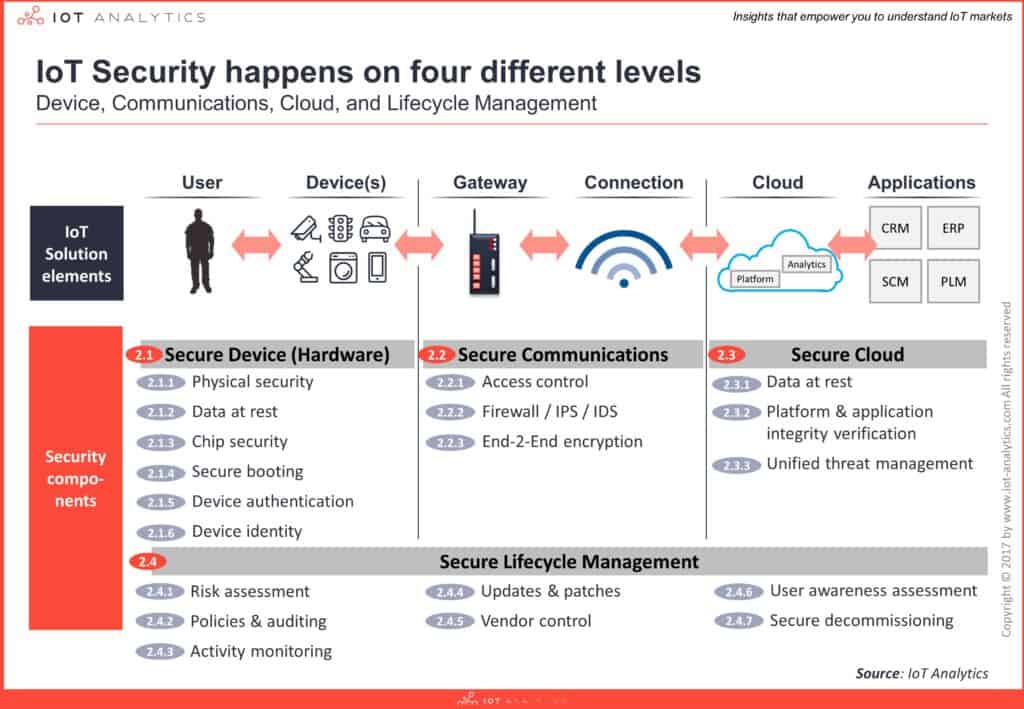
Satyajit Sinha: People are focused on securing devices that create critical data, autonomous driving and intelligent devices for example. But this should not just be about selected devices.
A thermostat may not provide critical data so you may disregard whether it is secured or not. But, if it is linked to your home gateway, it is easy for someone to hack into your network and get all the information from all other connected devices.
What is the strategy that will secure IoT?
Satyajit Sinha: For hackers, it is a business. They will not invest their time and money in devices with multiple layers of security. So, the best strategy is to have multiple layers of security from hardware to software to network to cloud security. Connect these four and create end-to-end security, also called chip-to-cloud security.
What are the challenges or roadblocks to securing IoT end-to-end?
Satyajit Sinha: First is having the right policies and regulations. There needs to be proper regulations and direction for security implementation in the market. The second is industry sentiment.
“Treating security as an extra cost will incur a burden in the long term. We need to understand that if you don’t spend on that extra secure element chip, you will have to pay more in a ransomware attack.”
Satyajit Sinha
Last is device provisioning and key management services for chip-to-cloud security. It is difficult to manage security especially if you switch between service providers.
What are the key similarities and differences between traditional IT security and IoT Security?
Satyajit Sinha: The similarity I believe is that both are accountable not just at the OEM level but also platform and the cloud level. The difference is that it is new for the IT industry to manage IoT security with multiple applications. There are many standards, and numerous players come up with their own solutions.
How much is post-quantum security relevant for now?
Satyajit Sinha: All IoT devices have a lifespan of about 10 to 15 years which means they are not capable of quantum security in the long run. Security needs to be future proof and there is no extra cost for adding quantum-level security so organisations should consider having it.
Click on the PodChat player to listen to Sinha on the state of the security of IoT devices in Asia.
- How adequately do you think current IoT ecosystems are secured, especially for unmanaged IoT devices?
- Are concerns around IoT security justified? Or Why does the IoT ecosystem require security?
- What is the strategy that will secure IoT?
- What are the challenges or roadblocks to securing IoT end-to-end?
- What are the key differences between traditional IT security and IoT Security?
- How much is post-quantum security relevant for now?


