PodChats for FutureIoT: Reducing IoT risks – Technologist
The Internet of Things remains a top priority. Market research firm IoT Analytics says IoT remains a top-three corporate technology priority even though artificial intelligence (AI) has taken over as the top technology priority. In surveys from PWC, KPMG, and BCG, respondents ranked IoT second or third after AI in terms of investment prioritization for emerging technologies, with AI coming in first across the board.
In the Asimily report, IoT Device Security in 2024: The High Cost of Doing Nothing, it was concluded that breach tactics continue to evolve, that routers have become the favourite attack vector accounting for 70% of IoT infections, and manufacturing continues to be the top target among industries.
Barry Mainz, CEO at Forescout, says in addition to the “millions of devices out there, sometimes you don’t even know where they are.”
He cited the incident where a hacker tampered with the runway lights at an airport in the United States causing near-crashes. He isn’t optimistic that such incidents will not happen again. He worries that there are more such incidents remain.
“Hackers are tired of trying to beat up on the well-protected traditional IT equipment,” he suggests, and are thus going after infrastructure that is less secure. He points out that IoT devices are a good target, given the volume out there, and many have never been designed (to be secure). He concedes that often unsecured IoT devices are only discovered after these have been hacked.
“How do you fix those things when the designers, developers or coders who created those things are no longer there?” he quipped.
Unsecured IoT – more prevalent than first thought
A 2022 Forrester Security Survey revealed that IoT devices were the most commonly reported target for external attacks, above employee- or corporate-owned mobile devices or computers (see Figure 1).
Figure 1: Most commonly reported target of external attacks
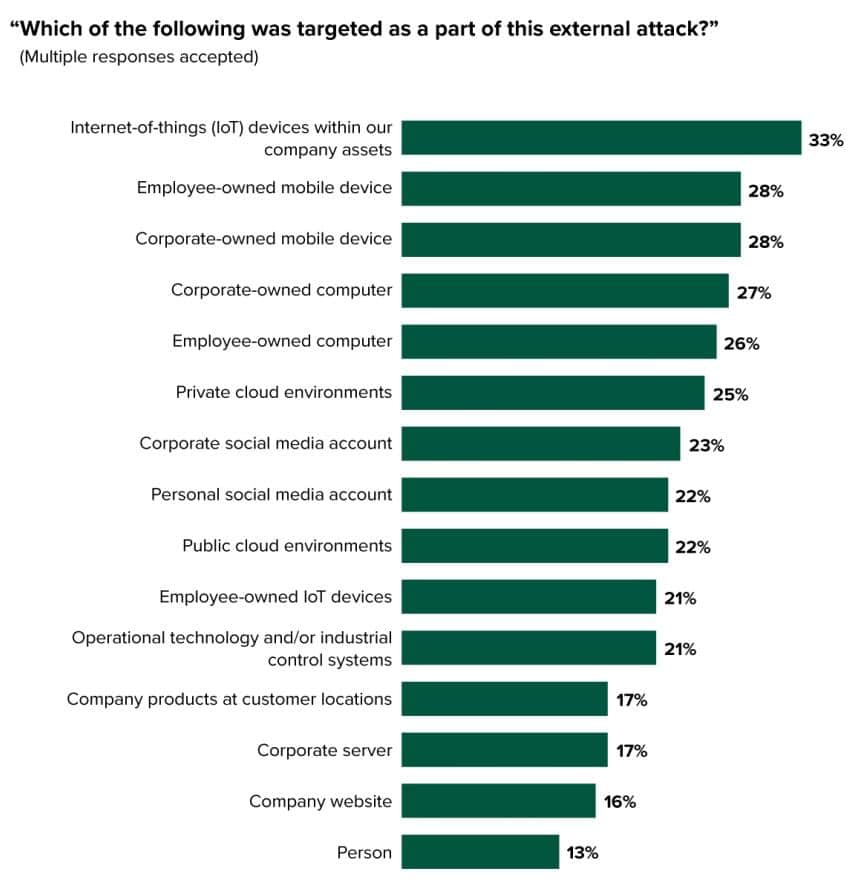
Source: Forrester’s Security Survey, 2022
In the State of IoT Security, 2023 report by Forrester, noted that the problem with IoT (security) is not the “T” but the “I” meaning that the device is connected to the Internet making it accessible for anyone looking for it.
“Because of this connectivity, if vulnerabilities arise and are not quickly resolved, IoT devices become a conduit for command-and-control attacks or become botnets, as shown with Mirai and its offshoots,” said Forrester.
Mainz observes that healthcare, manufacturing, financial services and government currently face the greatest risks from IoT. He cited the example of a customer engagement at a children’s hospital where it was revealed during a proof-of-value exercise about 1,000 unmanaged, unsecured devices, mostly gaming machines, that were connected to the hospital network.
The conundrum of securing IoT
Mainz concedes that identifying what is connected is only one part of the challenge. The more challenging aspect lies in understanding the level of risks each device presents. “It’s complicated because these environments are heterogeneous with many software and hardware vendors associated with these,” he added.
He also added that IoT has, historically, been under the purview of the operational technology team. CIOs and CISOs have always been focused on the information security side. “You have these two distinct groups of people or hubs of knowledge – they’re out there and have their vested interests in all that,” he opined.
Gartner estimates that over 80% of organisations have implemented IoT and yet less than a third of CISOs are confident their information security can reliably assess and mitigate cyber risk posed by IoT devices.
Mainz opines that transparency and bad news don’t age well. He reckons security will occur (eventually – not an if but a when). He suggests being very defensive in the approach towards IoT security. “And then you can go on the offensive after you take a look at the defensive,” he concluded.
Click on the PodChat player to hear Mainz elaborate on how to reduce IoT risks in 2024 and beyond.
- Can you give the key points of The Enterprise of Things Security Report by Fourscout Research Labs?
- What do we don’t know already about the insecurity of IoT devices and technologies?
- Some claim that breaches can occur by way of unsecured IoT devices. Can you confirm or elaborate on this?
- Given the rising level of awareness of the risks associated with enterprise IoT, what is being done? And if none, why?
- Where are the areas of IoT that present the greatest risks?
- Name 3 questions CIOs/heads of OT and security, need to ask as part of an IoT deployment.
- Recapping: Our topic is reducing IoT risks. Given what we know about IoT adoption trends, the evolving cyber threat landscape specific to IoT, and innovations in areas like machine learning and artificial intelligence, do we have any hope of reducing IoT risks, and can you name three action items for whoever should be responsible for securing enterprise IoT?
- You mentioned Fourscout coming in to look at an organisation’s assets to check for possible vulnerabilities. How are businesses receptive to this approach?


